AWS Single Sign-on (SSO) is a method of workforce authentication and authorization on AWS. The approach enables access to multiple AWS accounts and cloud applications with single credentials, which may be issued by external identity providers. Integrated with SSM Parameter Store – a secrets management solution – it provides a secure and effective way to store user credentials.
In this article, we will configure SSO with SSM Parameter Store in Terraform to grant users credentials to access a database.
How to make it
We use attributes in permission policies to determine who in our identity source can access our AWS resources. I specified the user’s FirstName and LastName as attributes to control access to SSM and added the attributes to SSO configuration. User information is retrieved from Google Workspace as an identity source at login.
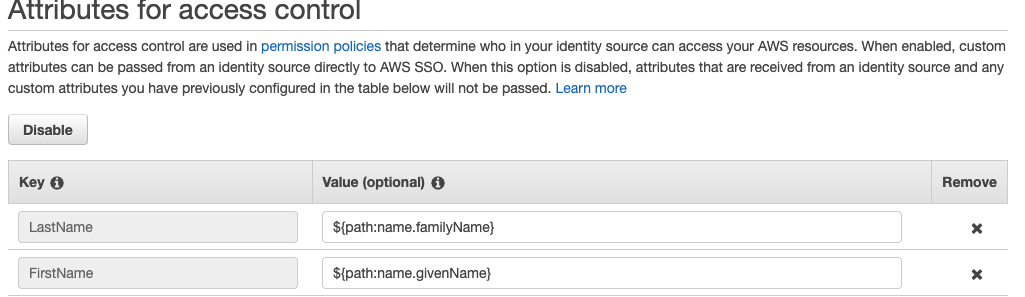
Then I created a custom policy that stipulates user access based on the attributes mentioned above and added it to the AWS SSO permission set – a list of permissions that acts as an IAM role in the target AWS account. My custom permission policy for SSM Parameter Store is as follows:
data "aws_iam_policy_document" "SSO4DevelopersBeta" {
statement {
sid = "AllowDescribeSSMParameters4SSOUsers"
actions = [
"ssm:DescribeParameters"
]
resources = [
"*"
]
}
statement {
sid = "GetOwnSSmCredentials4SSOUsers"
actions = [
"ssm:GetParameter"
]
resources = [
"arn:aws:ssm:us-east-1:your_account_id:parameter/$${aws:PrincipalTag/LastName}/$${aws:PrincipalTag/FirstName}/*"
]
condition {
test = "StringEquals"
variable = "ssm:resourceTag/LastName"
values = [
"$${aws:PrincipalTag/LastName}"
]
}
condition {
test = "StringEquals"
variable = "ssm:resourceTag/FirstName"
values = [
"$${aws:PrincipalTag/FirstName}"
]
}
}
}
Then I added the attributes FirstName and LastName to SSM parameters as tags to enable access to a database secret to specific users:
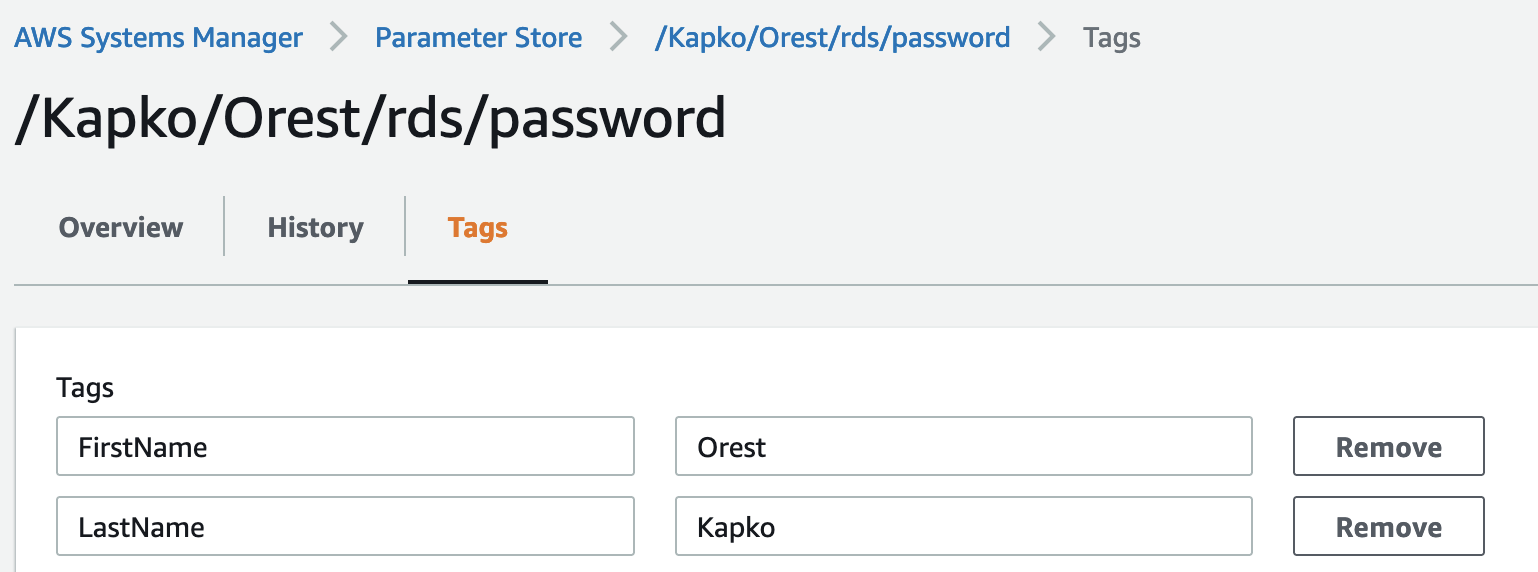
To further secure parameters, I added a restriction that users can only access those passwords whose path corresponds to their attributes, i.e. FirstName and LastName:
SSM PATH: /Kapko/Orest/rds/password >> TF statement: "arn:aws:ssm:us-east-1:YOUR_ACCOUNT_ID:parameter/$${aws:PrincipalTag/LastName}/$${aws:PrincipalTag/FirstName}/*"
When using multiple condition blocks, it is important to remember that AWS evaluates the conditions as though with an “AND” boolean operation. So, for the policy statement to apply, make sure that all condition blocks evaluate to true.
That’s it – by performing these simple steps I have integrated SSO with SSM Parameter Store and secured my database credentials from unauthorized access. Now users can access the secret per a unique path that corresponds to their attributes.
Conclusion
A combination of AWS SSO and SSM Parameter Store configuration is a secure and simple way to manage access to your AWS resources. It allows for centralized password management and enables system administrators to grant granular access for user credentials based on their attributes, without hardcoding permission policies.


